I want to do code array with topic bmi.....can you give one example?
DataSet’ is a ‘namespace’ but is used like a ‘type’
Error 1 'AdvoDiary.DataSet' is a 'namespace' but is used like a 'type' D:\AdvoDiary\AdvoDiary\ReportViewer\rptBilling.cs 25 9 AdvoDiary
namespace AdvoDiary.ReportViewer
public partial class rptBilling : Form
Common sCom;
DBHelper myDB;
string sOLE;
clsGlobalVar objGlob;
OleDbConnection cn;
OleDbDataAdapter sDA;
DataSet sDS;
OleDbCommand cmd;How to Choose a Content Layout for Your WordPress Blog
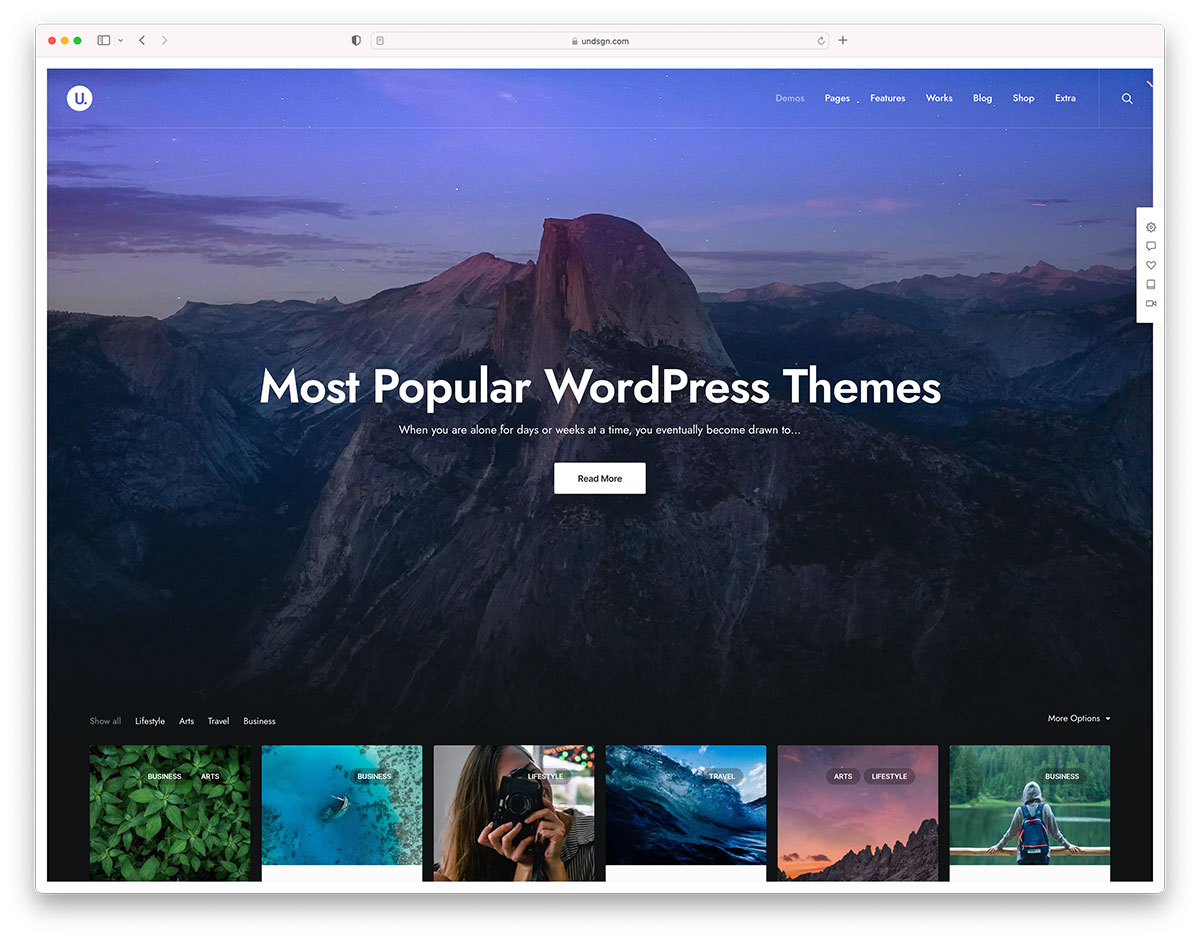
 When creating a blog, much of your focus will (rightfully) be on the content itself. However, how you’re presenting your content to the world matters, too. And we’re not just talking about the appearance or design here. The actual layout of how your content is presented can be instrumental in how site visitors interact with […]
When creating a blog, much of your focus will (rightfully) be on the content itself. However, how you’re presenting your content to the world matters, too. And we’re not just talking about the appearance or design here. The actual layout of how your content is presented can be instrumental in how site visitors interact with […]
The post How to Choose a Content Layout for Your WordPress Blog appeared first on WPExplorer.
This Week In Web Design – January 22, 2021
The Only WordPress SEO Checklist You’ll Need: 21 SEO Tips for 2021
Source: Pixabay Who can successfully launch and grow a business without investing in a powerful search engine optimization (SEO) strategy? Absolutely no one! Today’s competitive and consumer-driven market dictates that brands strive to stand out...
The post The Only WordPress SEO Checklist You’ll Need: 21 SEO Tips for 2021 appeared first on 85ideas.com.
Important Email Marketing Trends for 2022
This post is originally published on Designmodo: Important Email Marketing Trends for 2022

The way we conduct business and how we communicate with clients undergoes constant changes. A decade ago, people preferred face-to-face meetings in the office; today, even serious issues are easily addressed through Zoom. More and more people choose digital. However, …
For more information please contact Designmodo
How To Add Interactive Content To Your WordPress Site
 Millions of blog posts are published every single day on the WordPress platform alone. Standing out through your run-of-the-mill text article isn’t exactly easy. Integrating interactive content in your strategy for 2021 could be rather necessary to increase audience engagement. A Demand Gen study on content preferences found that B2B buyers are increasingly relying on […]
Millions of blog posts are published every single day on the WordPress platform alone. Standing out through your run-of-the-mill text article isn’t exactly easy. Integrating interactive content in your strategy for 2021 could be rather necessary to increase audience engagement. A Demand Gen study on content preferences found that B2B buyers are increasingly relying on […]
The post How To Add Interactive Content To Your WordPress Site appeared first on WPExplorer.
Are You a Designer? These 13 Top WordPress Themes Were Created for You
This post is originally published on Designmodo: Are You a Designer? These 13 Top WordPress Themes Were Created for You
Before taking that first step toward creating a new website you should have first given careful thought as to how you want it to look. The content has to be first-rate, and it has to be presented in a way …
For more information please contact Designmodo
an assignment that i am having trouble with coding
Write a program that prompts the user to input (word/statement), Accepts only letters. The program then: 1.Remove all the vowels from the (word /statement) then output the (word /statement) without vowels. 2. Outputs the number of vowels. 3. Convert the lowercase vowels letters to uppercase and vice versa. Conditions: 1. Use only (while Or do-while loop). Do everything outside the main function except declarations.
19 Great WordPress Knowledge Base & Wiki Themes
WordPress can be used to create any type of website. Thanks to thousands of themes and plugins, there is no …
19 Great WordPress Knowledge Base & Wiki Themes Read More →
The post 19 Great WordPress Knowledge Base & Wiki Themes first appeared on WP Superstars.Test Your WordPress Site Security – 6 Free WordPress Security Scanners
We think our security plugin, Defender, is pretty darn good, but we’d never tell you to put all your eggs in one basket. Even with a super-reliable and robust security plugin, you should still carry out extra checks on your site’s security…
Gone are the days where the only way to infiltrate someone’s computer or accounts was to send them a virus disguised as a pdf or manually guess their passwords.
Nowadays, hacking is easy. It’s automated.
Bots can brute-force their way into a site, create fake administrator accounts, and scan the network for vulnerabilities and valuable files in a matter of seconds.
This means that you no longer need a determined enemy in order to be the victim of an attack.
And since attacks are always on the rise, it makes sense to take whatever precautions are available in order to protect your site and ultimately, your visitors.
One of these precautions is simply taking the time to check your site from a few different sources.
Read on as we take a look at some of the best free tools out there.
1. Defender
2. WordPress Tools
3. wpRecon
4. VirusTotal
5. Mozilla Observatory
6. Google Transparency Report
1. Defender
Hopefully, you’re already using Defender to protect your site against malicious attacks, however, did you know it has an awesome scan feature, as well as a comprehensive rundown of things you can do to improve your site security?
Let’s start with the scan.
To begin a scan, click on Defender’s Malware Scanning option in the WordPress sidebar.

Defender will then highlight any files that it thinks are suspicious, such as core files which have been edited or don’t come as standard.

You’ll need to check through the files to decide whether they pose a risk, or whether they are changes you’ve made yourself.
You then have three options:
- If you don’t think a certain file should exist at all, you can delete it.
- If you believe a core file has been tampered with, you can restore it to the original – Defender will replace it with a fresh copy.
- If you trust these files, you can ask Defender to ignore them in future scans.

Ensuring that no code has been tampered with is a great way to keep on top of your site security.
Defender goes one step further. It can carry out an overall check on your site security to give you recommendations if there are vulnerabilities on your site that could easily be fixed.
Simply head to the Recommendations section to find out if Defender has picked up any vulnerabilities.

You can click on each item individually to see more information. Defender can even provide you with instructions to fix it!

Defender will also let you know what you’re doing right, by listing all the precautions you have already taken.
Simply navigate to the Actioned tab on the left of Defender’s screen.

Like what you see?
Check out our full guide on how to get the most out of Defender, and if you host with us, take a look at how it integrates perfectly with The Hub.
2. WordPress Tools
The WordPress Tools section might not be somewhere you check into often, however, the Site Health menu can be pretty valuable, and is worth the odd visit.
This tool also offers more than just security recommendations and will provide more information than any of the external tools as it is linked directly with your site.

If you click on each recommendation, you will get some pretty useful further details.

You can also check out the list of passed tests so that you know what you’re doing right.

It’s built right into your WordPress installation so it should only take a minute or two to carry out a quick check every once in a while.
3. wpRecon
It’s good to get an idea of any information about your site which is publicly accessible, as this can be used by hackers to find ways to compromise your security.
One of the best ways to find out what information is readily available is by using a third-party tool that isn’t linked to your site.
wpRecon is one of these tools.
Simply input the URL of the site you want to test.

The test will give you a variety of results, with the first set being in relation to your server type, IP address, and a check of the version of WordPress you’re running.

It will also inform you of any plugins that are reading the HTML source of the website’s front page, check for information it can find about the theme, and try to list the contents of uploads and plugins folders.

A routine check using a tool such as wpRecon will help you identify if there are any big holes, ready for hackers to walk through.
4. VirusTotal
VirusTotal is another free online tool for scanning sites, documents, and IP addresses. It has a database of over 70 antivirus scanners and URL/domain blacklisting services.

If your site is clean, you should be good to go, however, if any of the databases pick up something malicious, it could be that you have malware.
If this is the case, it could be worth running a full malware scan.
You can also check some further details regarding your site.

VirusTotal shares the result of the scan with the examining partners that it uses. This grows their virus and knowledge databases, helping to fight the fight against malware and hackers.
5. Mozilla Observatory
Mozilla Observatory is slightly different from the tools we’ve looked at above, as it offers a few separate types of tests.
When you first run the scan, it will test vulnerabilities in relation to HTTP. It will then give your site a score in the form of a letter.

Scroll down to see which of the tests you failed (if any).

Click on the name of each test to be taken to a page created by Mozilla which fully explains what it means.
After the first scan, you can also initiate further ones to check if access to your site can be gained through SSH (it would be very concerning if this was the case!) and extra tests with third-party companies ImmuniWeb, securityheaders.com, and hstspreload.org.
6. Google Transparency Report
Google’s Transparency Report isn’t really the answer for checking for vulnerabilities on your own site, however, there’s a reason it made it to this list.
The reason it won’t be much help when it comes to your own site is that it only tells you whether or not it finds anything unsafe, it doesn’t tell you what the unsafe content is.
This makes it pretty redundant when checking on your own site but can come in useful when checking a site you want to visit.
If you’re nervous about visiting a URL for the first time, you can simply input it into Google Transparency Report’s search bar, and let it check it out for you.

So yes, whilst it may not be the answer to checking for holes in your site security, it’s a pretty good tool to have in your bag!
Stay One Step Ahead
Carry out regular checks on your site using a variety of tools to make sure you identify any vulnerabilities before hackers or bots sniff them out.
Many of the issues picked up by these tools are quick and easy fixes, so schedule in regular checks as part of your site security process.
If you want to know how to make sure you haven’t missed anything when it comes to setting up the protection for your WordPress site, be sure to check out our 16-step checklist to total site lockdown.
And with this being #SecurityMonth you can currently get 35% off your first year of our Security & Backups Pack featuring Defender Pro, Snapshot Pro, Shipper Pro, and Automate. Click on the coupon below to unlock the exclusive deal.
35% Off Security & Backups Pack
Hello can anyone help me how to code this I really don’t know how to start

Sample output:
Enter number of guests: 40
40 guests have been invited.
Enjoy the party!
Creating package with functions in pl/sql
Hello all I am having problem with functions. Always getting Error(7,11): PLS-00323: subprogram or cursor 'EMPLOYEE_EMAIL' is declared in a package specification and must be defined in the package body. My package body.

Print each facebook ad campaign separate
Hey, I would need some help.
I use Facebook API to get all the Ad Campaigns that exist on my account.
I would want each ad campaign that exists, to print out seperatly, one ad campaign per box for example (https://emildeveloping.se/screenshots/POWERPNT_JcaaOq2NXx.png).
This is my code now: https://pastebin.com/HAjSD6Nr
This is the data I get back from $result2: https://pastebin.com/gXcBRRn
The errors I get with my code right now: https://emildeveloping.se/screenshots/Code_f2AMuMqZgO.png
All help is appricated.
On Auto-Generated Atomic CSS
Robin Weser’s “The Shorthand-Longhand Problem in Atomic CSS” in an interesting journey through a tricky problem. The point is that when you take on the job of converting something HTML and CSS-like into actual HTML and CSS, there are edge cases that you’ll have to program yourself out of, if you even can at all. In this case, Fela (which we just mentioned), turns CSS into “atomic” classes, but when you mix together shorthand and longhand, the resulting classes, mixed with the cascade, can cause mistakes.
I think this whole idea of CSS-in-JS that produces Atomic CSS is pretty interesting, so let’s take a quick step back and look at that.
Atomic CSS means one class = one job
Like this:
.mb-8 {
margin-bottom: 2rem;
}Now imagine, like, thousands of those that are available to use and can do just about anything CSS can do.
Why would you do that?
Here’s some reasons:
- If you go all-in on that idea, it means that you’ll ship less CSS because there are no property/value pairs that are repeated, and there are are no made-up-for-authoring-reasons class names. I would guess an all-atomic stylesheet (trimmed for usage, which we’ll get to) is a quarter the size of a hand-authored stylesheet, or smaller. Shipping less CSS is significant because CSS is a blocking resource.
- You get to avoid naming things.
- You get some degree of design consistency “for free” if you limit the available classes.
- Some people just prefer it and say it makes them faster.
How do you get Atomic CSS?
There is nothing stopping you from just doing it yourself. That’s what GitHub did with Primer and Facebook did in FB5 (not that you should do what mega corporations do!). They decided on a bunch of utility styles and shipped it (to themselves, largely) as a package.
Perhaps the originator of the whole idea was Tachyons, which is a just a big ol’ opinionated pile of classes you can grab as use as-is.
But for the most part…
Tailwind is the big player.
Tailwind has a bunch of nice defaults, but it does some very smart things beyond being a collection of atomic styles:
- It’s configurable. You tell it what you want all those classes to do.
- It encourages you to “purge” the unused classes. You really need to get this part right, as you aren’t really getting the benefit of Atomic CSS if you don’t.
- It’s got a UI library so you can get moving right away.
Wait weren’t we talking about automatically-generated Atomic CSS?
Oh right.
It’s worth mentioning that Yahoo was also an early player here. Their big idea is that you’d essentially use functions as class names (e.g. class="P(20px)") and that would be processed into a class (both in the HTML and CSS) during a build step. I’m not sure how popular that got really, but you can see how it’s not terribly dissimilar to Tailwind.
These days, you don’t have to write Atomic CSS to get Atomic CSS. From Robin’s article:
It allows us to write our styles in a familiar “monolithic” way, but get Atomic CSS out. This increases reusability and decreases the final CSS bundle size. Each property-value pair is only rendered once, namely on its first occurence. From there on, every time we use that specific pair again, we can reuse the same class name from a cache. Some libraries that do that are:
• Fela
• Styletron
• React Native Web
• Otion
• StyleSheetIn my honest opinion, I think that this is the only reasonable way to actually use Atomic CSS as it does not impact the developer experience when writing styles. I would not recommend to write Atomic CSS by hand.
I think that’s neat. I’ve tried writing Atomic CSS directly a number of times and I just don’t like it. Who knows why. I’ve learned lots of new things in my life, and this one just doesn’t click with me. But I definitely like the idea of computers doing whatever they have to do to boost web performance in production. If a build step turns my authored CSS into Atomic CSS… hey that’s cool. There are five libraries above that do it, so the concept certainly has legs.
It makes sense that the approaches are based on CSS-in-JS, as they absolutely need to process both the markup and the CSS — so that’s the context that makes the most sense.
What do y’all think?
The post On Auto-Generated Atomic CSS appeared first on CSS-Tricks.
You can support CSS-Tricks by being an MVP Supporter.
This Week In Web Design – January 15, 2021
computer question
Score calculation
1.1 Write a function in Matlab that accepts the degree of writing as input arguments
bg and the degree of work be and return the final degree bt, which is calculated as o
average grades of work and writing with the following exceptions:
i. If the grade of the writing is zero then the final grade is 0.
ii. If the writing grade is less than 3, then the final grade is the average
if the average is less than 4, or otherwise 4.
iii. If the grade of the work is less than 5, then the final grade is the average
if the average is less than 4, or otherwise 4.
The final score will be rounded to the nearest whole number using the round (x) function.
1.2 Change the function so that it accepts registers as arguments.
How To Save Images From Google Docs (3 Methods)
Are you looking for a way to save images from Google Docs? If you have ever tried to save an …
How To Save Images From Google Docs (3 Methods) Read More →
The post How To Save Images From Google Docs (3 Methods) first appeared on WP Superstars.