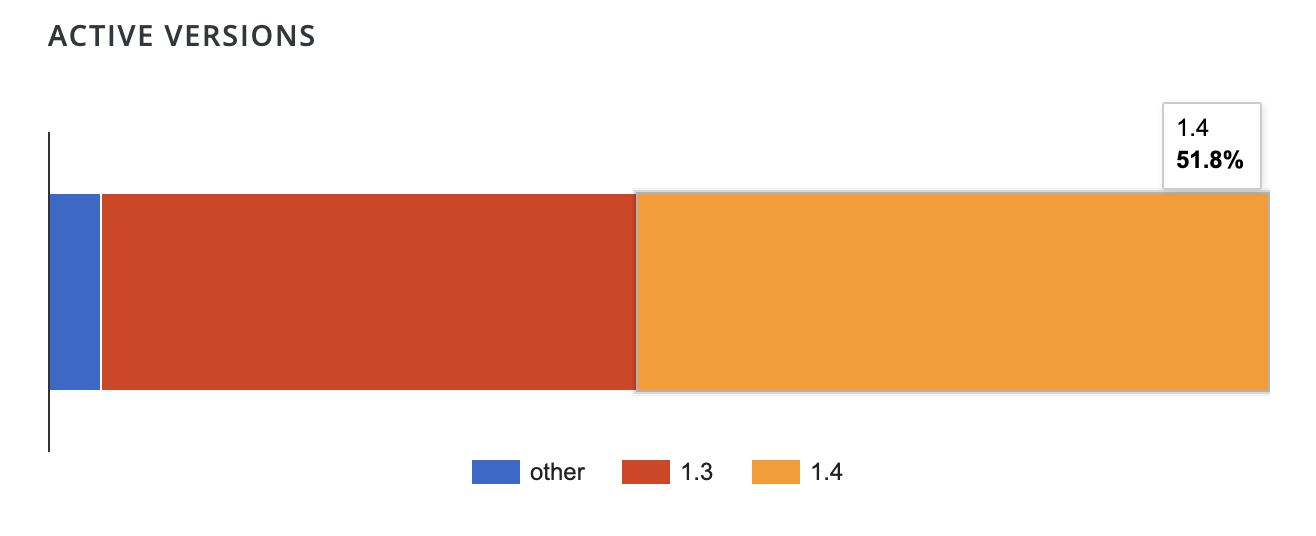
WooCommerce 4.6.2 was released yesterday with a fix for a vulnerability that allowed account creation at checkout, even when the “Allow customers to create an account during checkout” setting is disabled. The WooCommerce team discovered it after several dozen users reported their sites were receiving spam orders, or “failed orders” where the payment details were fake.
WooCommerce developer Rodrigo Primo described how the bot is attacking stores:
The gist of it is that the bot is able to create a user when placing an order exploiting the bug fixed by 4.6.2. After creating the user, the bot tries to find vulnerabilities in other plugins installed on the site that require an unprivileged authenticated account.
WooCommerce recommends users update to 4.6.2 to stop bots from creating users at checkout and then remove any accounts the bot previously created. This will not stop the bots from creating fake orders so store owners are advised to install additional spam protection from the WooCommerce Marketplace. Some users in the support forum are trying free plugins like Advanced noCaptcha & Invisible Captcha and Fraud Prevention Plugin for WooCommerce.
The first logged instance happened nine days before WooCommerce was able to issue a fix. In the meantime, some users reported having their site’s URL changed and other hacking attempts. Dave Green, WordPress engineer at Make Do, used log files to determine that the script relies on exploiting other vulnerabilities in order to gain access to the database.
“That script is creating the order, and is also likely to be exploiting whatever vulnerability is available to bypass customer account settings and create a new user; it may or may not be relying upon other exploits for this,” Green said.
“Assuming it has successfully gained access to the system, it then tries to update the DB. It either fails and leaves you with nuisance orders, or succeeds and points your site to the scam URL.”
The WooCommerce team has also fixed this same bug in WooCommerce Blocks 3.7.1, preventing checkout from creating accounts when the related setting is disabled.
WooCommerce did not publish the names of any of extensions that have vulnerabilities being exploited by this script. However, some one user reported an attack that coincided with the fake orders:
I had a failed order yesterday with similar info to the OP as well.
At the exact same time that failed order came in, my WAF blocked two attempted attacks from the same user/IP (bbbb bbbb) for “TI WooCommerce Wishlist < 1.21.12 – Authenticated WP Options Change”
The script may have been probing for a vulnerability in the TI WooCommerce Wishlist plugin, which was patched approximately two weeks ago. The plugin is active on more than 70,000 WordPress sites.
The WooCommerce team is still researching the origin and impact of this vulnerability and will publish more information as it becomes available.


 WordPress is a powerful content management system (CMS) by all means, but it comes with its fair share of debilitating errors. Just like any other human-made system, it’s prone to errors that can result from many different things. Perhaps you installed a faulty theme or plugin and messed up your install. Maybe a natural disaster […]
WordPress is a powerful content management system (CMS) by all means, but it comes with its fair share of debilitating errors. Just like any other human-made system, it’s prone to errors that can result from many different things. Perhaps you installed a faulty theme or plugin and messed up your install. Maybe a natural disaster […]


 It’s a stroke of luck for mischief makers on the internet if they can find a way to harm WordPress websites. With just one trick up their sleeves, they can take a shot at almost 30% of the websites on the internet. That’s the downside of WordPress being the most popular CMS. As website owners, […]
It’s a stroke of luck for mischief makers on the internet if they can find a way to harm WordPress websites. With just one trick up their sleeves, they can take a shot at almost 30% of the websites on the internet. That’s the downside of WordPress being the most popular CMS. As website owners, […] Did you know over 100,000 websites are hacked daily? That’s right, cybercrime is a serious threat to any company, and anybody with a WordPress site isn’t safe either. I have had a run-in with hackers (and had to recover my WordPress site), and you probably know it was ugly. Hackers are actively looking for vulnerable […]
Did you know over 100,000 websites are hacked daily? That’s right, cybercrime is a serious threat to any company, and anybody with a WordPress site isn’t safe either. I have had a run-in with hackers (and had to recover my WordPress site), and you probably know it was ugly. Hackers are actively looking for vulnerable […]